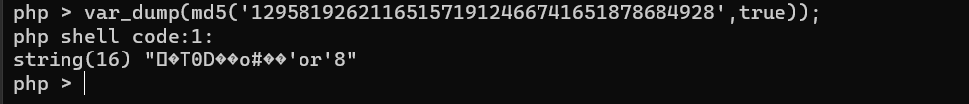
参考:https://blog.csdn.net/zz_Caleb/article/details/84947371 md5的碰撞,在PHP的数的处理中,0开头的字符串会被转换成0,所以才会有md5碰撞。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 0e开头的md5和原值: QNKCDZO 0e830400451993494058024219903391 s878926199a 0e545993274517709034328855841020 s155964671a 0e342768416822451524974117254469 s214587387a 0e848240448830537924465865611904 s214587387a 0e848240448830537924465865611904 s878926199a 0e545993274517709034328855841020 s1091221200a 0e940624217856561557816327384675 s1885207154a 0e509367213418206700842008763514 s1502113478a 0e861580163291561247404381396064 s1885207154a 0e509367213418206700842008763514 s1836677006a 0e481036490867661113260034900752 s155964671a 0e342768416822451524974117254469 s1184209335a 0e072485820392773389523109082030 s1665632922a 0e731198061491163073197128363787 s1502113478a 0e861580163291561247404381396064 s1836677006a 0e481036490867661113260034900752 s1091221200a 0e940624217856561557816327384675 s155964671a 0e342768416822451524974117254469 s1502113478a 0e861580163291561247404381396064 s155964671a 0e342768416822451524974117254469 s1665632922a 0e731198061491163073197128363787 s155964671a 0e342768416822451524974117254469 s1091221200a 0e940624217856561557816327384675 s1836677006a 0e481036490867661113260034900752 s1885207154a 0e509367213418206700842008763514 s532378020a 0e220463095855511507588041205815 s878926199a 0e545993274517709034328855841020 s1091221200a 0e940624217856561557816327384675 s214587387a 0e848240448830537924465865611904 s1502113478a 0e861580163291561247404381396064 s1091221200a 0e940624217856561557816327384675 s1665632922a 0e731198061491163073197128363787 s1885207154a 0e509367213418206700842008763514 s1836677006a 0e481036490867661113260034900752 s1665632922a 0e731198061491163073197128363787 s878926199a
MD5值(哈希值)相等的问题可以用哈希值碰撞,也可以用数组绕过,如:username[]=1&password[]=2.
sha1也一样
1 2 3 4 sha1('aaroZmOk') sha1('aaK1STfY') sha1('aaO8zKZF') sha1('aa3OFF9m')
———————————–2020.8.4更新—————————————-
1 2 3 4 content:ffifdyop hex:276f722736c95d99e921722cf9ed621c raw:'or' 6\xc9]\x99\xe9!r,\xf9\xedb\x1c string:'or' 6]!r,b
可用于某些ctf题目的sql注入
1 content:129581926211651571912466741651878684928
———————————-2020.8.14更新—————————————-
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 import hashlibimport randomdef encryption (chars ): return hashlib.md5(chars).hexdigest() def generate (): return str(random.randint(99999 ,1000000 )) def main (): start = "5e" while True : strs = generate() print "Test %s " % strs if encryption(strs).startswith(start): print "yes!" print "[+] %s " % strs + "%s " % encryption(strs) break else : print "no!" if __name__ == '__main__' : main() print '完成!'
另一个md5碰撞脚本,具有md5双碰撞功能
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 import multiprocessingimport hashlibimport randomimport stringimport sysCHARS = string.letters + string.digits def cmp_md5 (substr, stop_event, str_len,. start=0 , size=20 ): global CHARS while not stop_event.is_set(): rnds = '' .join(random.choice(CHARS) for _ in range(size)) md5 = hashlib.md5(rnds) value = md5.hexdigest() if value[start: start+str_len] == substr: print rnds stop_event.set() ''' #碰撞双md5 md5 = hashlib.md5(value) if md5.hexdigest()[start: start+str_len] == substr: print rnds+ "=>" + value+"=>"+ md5.hexdigest() + "\n" stop_event.set() ''' if __name__ == '__main__' : substr = sys.argv[1 ].strip() start_pos = int(sys.argv[2 ]) if len(sys.argv) > 1 else 0 str_len = len(substr) cpus = multiprocessing.cpu_count() stop_event = multiprocessing.Event() processes = [multiprocessing.Process(target=cmp_md5, args=(substr, stop_event, str_len, start_pos)) for i in range(cpus)] for p in processes: p.start() for p in processes: p.join()
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 import hashlibimport reprefix = '0e' def breakit (): iters = 0 while 1 : s = prefix + str(iters) hashed_s = hashlib.md5(s).hexdigest() iters = iters + 1 r = re.match('^0e[0-9]{30}' , hashed_s) if r: print "[+] found! md5( {} ) ---> {}" .format(s, hashed_s) print "[+] in {} iterations" .format(iters) exit(0 ) if iters % 1000000 == 0 : print "[+] current value: {} {} iterations, continue..." .format(s, iters) breakit()
md5(0e215962017)=0e291242476940776845150308577824
还有一种文件内容不同,但是MD5值相同的利用方法
参考链接:https://www.cnblogs.com/wysngblogs/p/15905398.html
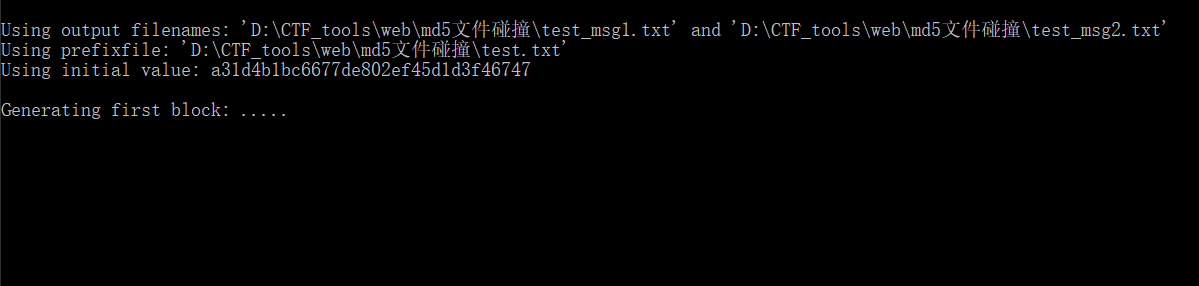
创建一个test.txt,随意输入字符串,拖入fastcoll
生成两个txt
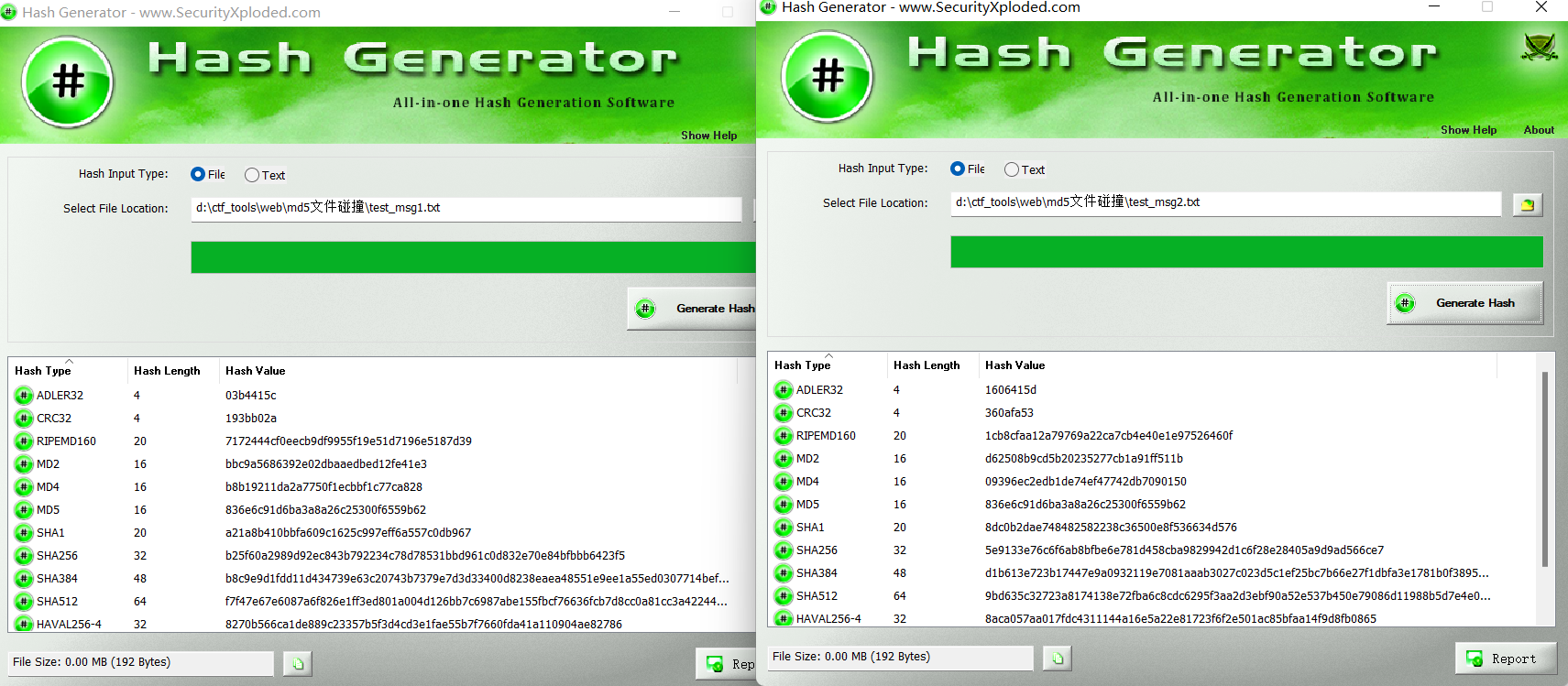
此时查看生成的md5值是一样的,可以用于绕过某些情况